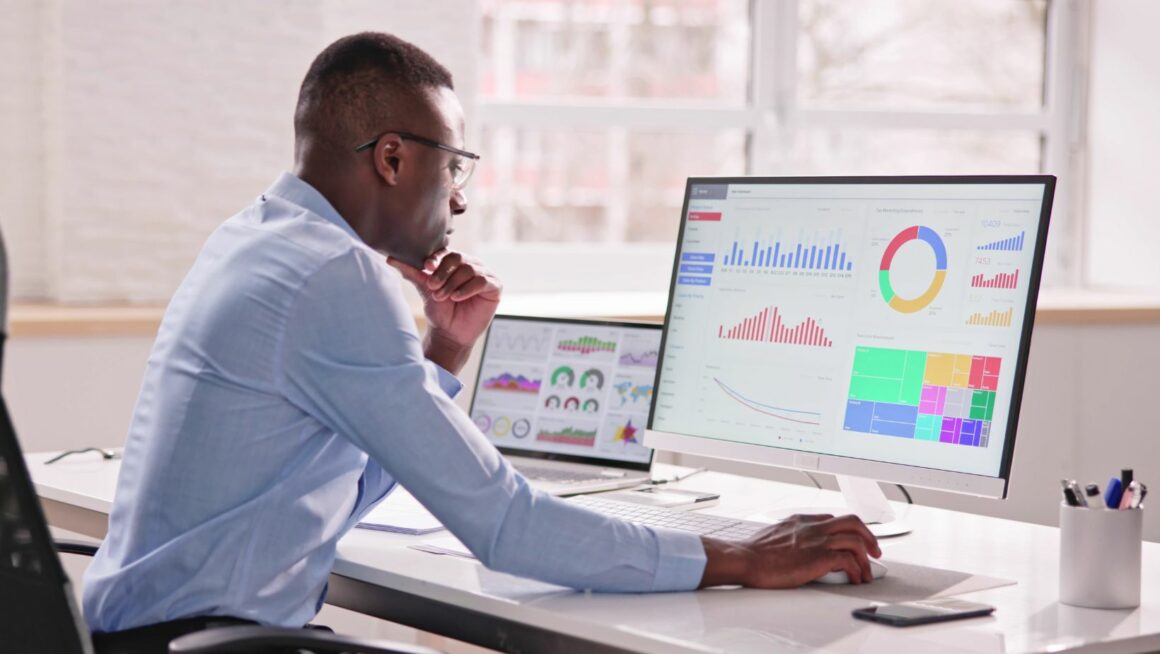
In today’s digital world, cybersecurity is more important than ever. Businesses and organizations face a constant battle against cyber threats, which evolve rapidly, making it essential to stay ahead of the curve. One of the most effective ways to protect your business from cyber-attacks is by using a threat intelligence platform. These platforms provide the tools and information needed to detect, analyze, and respond to potential threats before they can cause harm.
However, not all threat intelligence platforms are created equal. To get the most out of these tools, it’s important to understand the key features to look for. In this article, we’ll go over the top features that make a threat intelligence platform effective, helping you choose the right solution for your needs.
Real-Time Threat Data
One of the most crucial features of any threat intelligence platform is its ability to provide real-time threat data. The digital landscape is constantly changing, and threats can emerge at any moment. With real-time data, a platform can alert you to potential risks as soon as they appear, allowing you to take immediate action. This means less time spent reacting to threats and more time proactively defending your business.
Without real-time updates, threat intelligence is essentially outdated and could result in delays in addressing issues, leaving your organization vulnerable. Therefore, it’s essential to ensure that the platform you choose provides current, actionable information at all times.
Automated Threat Detection
Threat intelligence platforms should be able to automatically detect threats based on patterns and behaviors. This feature is critical because manual monitoring of security data can be time-consuming and prone to error. Automation helps speed up the process of identifying potential risks by using machine learning and algorithms that can recognize suspicious activity faster and more accurately than human eyes alone.
For example, the platform might use automated processes to flag unusual network behavior, new malware signatures, or suspicious IP addresses without any human intervention. This allows your security team to focus on addressing the threats instead of spending time on detection.
Integration with Other Security Tools
Another important feature to look for is integration capabilities. A threat intelligence platform should seamlessly integrate with other security tools that you are already using, such as firewalls, intrusion detection systems, and endpoint security software. This integration ensures that all aspects of your security system work together, providing a more comprehensive defense against threats.
For instance, if a threat intelligence platform detects a potential attack, it should be able to communicate this information to other tools in your security stack, triggering automatic responses like blocking malicious IP addresses or isolating affected systems. This coordination helps streamline your security processes and increases the speed and effectiveness of your responses.
Threat Analysis and Contextualization
Collecting raw data on potential threats is just the beginning. To make that data actionable, a threat intelligence platform must be able to analyze and contextualize it. This feature allows the platform to prioritize threats based on their severity, relevance, and potential impact on your organization.

Rather than simply providing a list of threats, a good platform will analyze these threats in context, helping you understand the nature of the risk, the possible attackers, their motives, and how they might attempt to exploit vulnerabilities. This deeper analysis makes it easier for your team to focus on the most pressing threats and respond more effectively.
For example, if a platform identifies a new type of malware, it will not only alert you to its presence but will also provide details on its behavior, its origin, and its potential impact on your systems, enabling a more targeted defense strategy.
Threat Intelligence Sharing
Cybersecurity is a collective effort, and no one organization can fight threats alone. That’s why threat intelligence sharing is an essential feature of any platform. A good threat intelligence platform will allow for easy sharing of intelligence with trusted partners, industry groups, and other organizations.
Sharing threat information helps everyone involved stay updated on the latest threats and trends, which can help prevent future attacks. This type of collaboration is especially important in industries that are commonly targeted, such as finance, healthcare, and government. By sharing intelligence, your organization becomes part of a broader network of cybersecurity awareness and defense.
Customizable Alerts and Notifications
Every business has different needs when it comes to cybersecurity. A threat intelligence platform should allow you to customize alerts and notifications based on your specific requirements. Whether it’s adjusting the sensitivity of alerts or setting up specific thresholds for triggering notifications, customization ensures that your team is only notified about the most important threats, reducing alert fatigue.
This feature also helps you avoid missing critical alerts that could otherwise be drowned out by a flood of irrelevant notifications. It allows you to focus on the threats that matter most to your business, ensuring a more efficient use of your resources.
Threat Intelligence Enrichment
Threat intelligence enrichment is another key feature that can significantly improve the effectiveness of a threat intelligence platform. This feature enhances the raw data collected by the platform by cross-referencing it with external sources, such as threat feeds, commercial threat data, and open-source intelligence.
Enrichment helps provide a fuller picture of each threat, adding additional context and insights that can be used to improve your response strategy. For example, if a platform identifies an IP address associated with a known hacker group, enrichment might reveal additional information about their past attacks, tactics, and tools, giving your team the information needed to prepare and respond.
Historical Data and Threat Correlation
In addition to real-time data, having access to historical data is essential for identifying long-term trends and understanding how threats evolve over time. A good threat intelligence platform will provide access to historical threat data and allow you to correlate current threats with past incidents.
This historical analysis helps you identify patterns and trends in attacks, which can inform your future security strategies. For instance, if you notice that certain types of attacks increase in frequency during specific times of the year, you can adjust your defenses accordingly, strengthening your organization’s security posture.
User-Friendly Interface
A threat intelligence platform might offer all the best features in the world, but if the interface is difficult to use, it could hinder your team’s ability to respond to threats effectively. A user-friendly interface is crucial for making the platform accessible to all users, regardless of their technical expertise.

The platform should offer intuitive dashboards, easy-to-read reports, and a clear navigation structure. It should also provide users with easy access to key features, such as threat detection, analysis, and response tools. A simple, well-designed interface makes it easier for your team to stay on top of potential threats and quickly take action when necessary.
Scalability and Flexibility
As your organization grows, so will your cybersecurity needs. A threat intelligence platform should be scalable, meaning it can grow with your business. It should also be flexible enough to adapt to changing security requirements, whether you’re expanding to new locations, adding new technologies, or facing evolving threats.
Scalability ensures that your platform can handle increasing amounts of data and traffic without losing performance. Flexibility ensures that the platform can adapt to new use cases, such as cloud environments, mobile devices, and other emerging technologies. With a scalable and flexible platform, your cybersecurity efforts will be able to evolve alongside your business.
Conclusion
Choosing the right threat intelligence platform is an important decision that can significantly impact your organization’s security posture. By focusing on features like real-time threat data, automated detection, integration with other security tools, contextual analysis, and threat intelligence sharing, you can ensure that you are getting the most value from your platform.
Remember, cybersecurity is an ongoing effort, and having the right tools in place is crucial for staying ahead of evolving threats. By considering these top features, you can make an informed decision and select a platform that meets your needs and protects your business from the ever-present risk of cyber-attacks.